Understanding How Phishing Links Work
In today’s digital era, comprehending how phishing links work is crucial for safeguarding your online information. Phishing links are a prevalent cyber threat aimed at deceiving users into revealing sensitive data. This guide explores their mechanisms, highlighting the tactics employed by cybercriminals to execute these attacks.
Phishing links often masquerade as legitimate URLs, exploiting human trust to circumvent security systems. One common method is email phishing, where users are misled into clicking deceptive links. Understanding this common technique can demystify how these malicious links operate.
Besides email phishing, various types of phishing attacks exist, each employing unique strategies. Recognizing and differentiating these attacks is the first step toward effective prevention. We’ll also introduce tools and tips to help you identify and block these threats.
Finally, you’ll gain practical strategies and resources, such as AntiPhish.AI, to enhance your defenses against phishing attacks. Whether you’re new to technology or a cybersecurity enthusiast, this guide offers valuable insights to help you navigate the web securely and protect your digital presence. Embrace this knowledge and fortify your online safety today!
Understanding Phishing and How Links Work
Phishing is a prevalent cyber attack tactic that leverages social engineering to deceive individuals into divulging sensitive information. Cybercriminals frequently masquerade as reputable entities, such as banks or companies, to gain access to login credentials, account numbers, or personal data.
Even with advancements in cybersecurity, phishing continues to thrive due to its simplicity and effectiveness. Attackers often send emails filled with misleading links that can bypass traditional security measures, exploiting human tendencies and the inherent trust individuals place in recognized brands.
This form of cybercrime is constantly evolving, which complicates detection efforts. Many fraudulent emails imitate established brands, enhancing their legitimacy and encouraging interactions from unsuspecting recipients. As a result, phishing constitutes a staggering 43% of global cyberattacks, particularly targeting sectors like finance, healthcare, and retail, which together comprise 66% of these occurrences.
The repercussions are severe, with significant financial losses that damage reputations and erode customer trust—losses can soar to $17,700 per minute during an attack. Knowing how phishing links work is vital for defense against such threats. Next, we will delve into the technical workings of these links and their strategies to ensnare users.
How Do Phishing Links Work
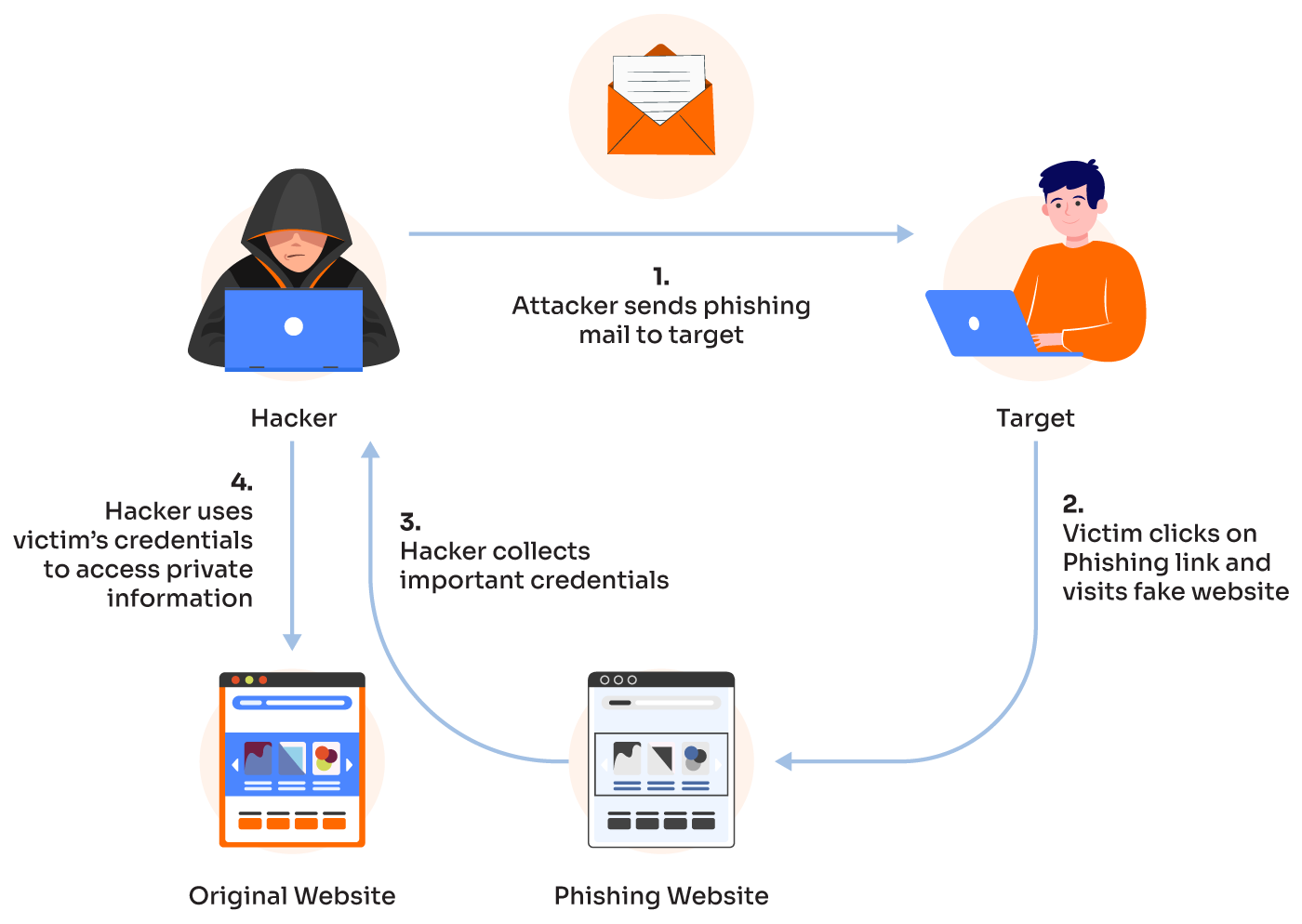
Phishing links are designed to exploit user trust and play a central role in online scams. They often redirect users to counterfeit websites that mimic real ones closely, from the logos to the interface. These fake sites solicit sensitive information like passwords by posing as routine verification from trusted companies.
Phishing relies heavily on psychological tactics. Scammers create a sense of urgency, fear, or curiosity, urging users to act quickly. Emails claiming suspicious activity on accounts or offering exclusive deals often lead users to click without thoroughly examining the source.
Email spoofing is another method used by phishers, where emails are disguised to appear as if they’re from trusted sources. By mimicking company branding and language, these emails lower recipients’ defenses against scams. Similarly, URL manipulation involves slight alterations to web addresses. For instance, changing “bankname.com” to “bannokname.com” can trick users into visiting a fraudulent site. These small modifications are often masked by subdomains and hyphens, trapping users who aren’t vigilant.
Additionally, clicking on phishing links can trigger the download of harmful software, or malware. This malware can capture keystrokes or even lock devices until a ransom is paid, underscoring the risks of indiscriminate clicking. Understanding these tactics helps enhance digital safety by promoting cautious online behavior.
Email Phishing: A Leading Threat
Email phishing is a common tactic used by cybercriminals, who exploit our familiarity with email. Through technical tricks and social tactics, these criminals manipulate victims into taking harmful actions. They rely on several methods that capitalize on trust and urgency to deceive individuals.
- Email Spoofing: Deceptive Sender IDs
- Compromised URLs: Fake Sites
- Risky Downloads: Harmful Attachments
- Urgent Language: Provoking Immediate Action
This method involves faking the sender’s address to appear as someone trustworthy. By pretending to be a credible source, they trick users into believing the message is legitimate, laying the groundwork for successful phishing attempts.
Phishing emails often contain links to fake websites mimicking legitimate ones, such as banks, to steal login details. The URLs are cleverly disguised to hide these traps effectively.
Attachments may carry malware and, once opened, grant hackers access to networks. This strategy proves effective during busy email periods, such as tax season or large sales events.
These emails use alarming language to pressure users into quick action, often regarding security or payment issues. The fear-based approach causes hurried, uncritical responses.
Understanding how phishing links work is crucial for protecting yourself from evolving cyber threats. Staying vigilant in email interactions can help you spot and prevent these harmful attempts.
Types of Phishing Attacks
Understanding the varied types of phishing attacks is crucial to recognizing how phishing links work and the strategies hackers employ to exploit individuals. These attacks are designed to exploit unnoticed vulnerabilities using cunning methods.
- Spear Phishing: By targeting specific individuals or organizations and using personal information from social media or previous communications, attackers make their messages convincing and difficult to identify as malicious.
- Whaling: This is a refined version of spear phishing aimed at high-ranking executives. Attackers masquerade as trusted contacts to gain sensitive company data or financial information.
- Smishing: Involves attacks through SMS messages that direct users to harmful links under false pretenses, like misleading claims about bank accounts or delivery issues.
- Vishing: Here, attackers use phone calls to impersonate legitimate figures, intending to collect personal, financial, or confidential details.
- Angler Phishing: On social media platforms, cybercriminals pretend to be brands or customer service accounts, deceiving users into sharing information through private messages.
Understanding these phishing techniques is key to staying alert. In the next section, Recognizing Phishing Emails and Links, we’ll explore ways to identify and steer clear of these threats effectively.
Understanding Phishing Emails and Links
Gaining insight into how phishing links work is crucial for staying safe online. Phishing tactics may evolve, yet certain indicators remain constant. Being aware of these can help you spot potential threats.
One red flag is unusual spellings or strange subdomains in URLs. Phishers often mimic genuine site addresses by tweaking letters or using alternative top-level domains. Another telltale sign is the use of public email domains like Yahoo or Gmail, rather than reputable corporate domains, to request personal information. Treat such emails with caution.
Poor language or grammatical errors can also be a giveaway. Many attackers don’t write fluently, leading to awkward phrases that betray their intent. Hovering over hyperlinks without clicking can reveal misleading destinations. Always be wary of URLs directing to unexpected or dubious websites.
Recognizing these signs enhances your defense against phishing. Utilizing tools like AntiPhish.AI offers added protection against these ongoing digital threats.
How Do Phishing Links Work?
Phishing attacks rely heavily on deception, using fake links to steal sensitive information. These links often resemble legitimate ones but aim to manipulate recipients into costly errors. So, how do phishing links operate?
Typically, these malicious links mimic real URLs. Cybercriminals employ techniques such as URL masking and character substitution to craft links that look genuine. For instance, they swap similar-looking letters or add sneaky subdomains to fool users into trusting them.
Upon clicking these fraudulent links, users are often redirected to a counterfeit site designed to imitate a familiar service. This fake website’s primary goal is to collect sensitive information, such as login credentials or financial data. The repercussions of sharing such data can be unauthorized access or theft, underscoring the risks associated with these links.
Beyond just data theft, encountering phishing links can lead to harmful software, like ransomware or trojans, being installed on a device, posing significant long-term risks.
Understanding how phishing links work is crucial for defense. Vigilance towards peculiar URLs, spelling errors, or strange domains can provide critical clues to spot these threats.
Moreover, advancements like AntiPhish.AI are improving detection by using AI to scrutinize emails and links. Staying informed and embracing such technologies is vital as phishing techniques continue to evolve.
Conclusion
In today’s digital landscape, understanding how phishing links work is crucial. Cybercriminals often use these deceptive links to trick users into compromising their online security. We’ve unpacked how email phishing schemes operate and the serious threats they pose.
Identifying phishing emails and dubious links is your first line of defense. Start by scrutinizing the source of the email and pausing before you click on any link. Consider employing specialized tools like AntiPhish.AI for added security during your online interactions.
With this insight into phishing links, you are better equipped to protect yourself and inform others. Promoting awareness fosters a safer online environment. Staying alert and prepared is essential as digital threats evolve. Use these guidelines to safeguard your personal information. By taking proactive steps, you can confidently navigate the digital world with greater peace of mind.
About AntiPhish.AI
AntiPhish.AI is a powerful Chrome extension crafted to safeguard Gmail users from phishing threats by rigorously analyzing email content, sender details, and embedded links to identify and block malicious activities. Offering real-time protection with advanced AI-driven algorithms, AntiPhish.AI delivers a seamless and intuitive user interface, ensuring your sensitive information remains shielded from cyber threats and identity theft.
In today’s digital age, where the frequency of phishing attacks is rapidly rising, AntiPhish.AI represents a crucial shield in the defense against cybercriminals, offering peace of mind to users without demanding technical proficiency.
Protect your inbox today by exploring AntiPhish.AI and experience secure emailing like never before!