In today’s digital world, understanding how phishing scams work is crucial. These deceptive cyber tactics target anyone, from online shoppers to casual browsers, with the aim of exploiting trust to access confidential information such as passwords and credit card details. Scammers often use various tricks, such as misleading emails and fake web links, to fool individuals into disclosing private data.
To protect yourself, it’s important to stay informed about the different methods scammers use. Our guide delves into the structure of phishing scams, highlighting key types like spear phishing and smishing. Each technique is crafted to deceive targeted users, making awareness the first line of defense. By learning about these tactics, you can better prepare and protect against potential threats.
Additionally, we offer practical prevention strategies that can aid in resisting such scams. Utilizing tools like AntiPhish.AI provides an extra layer of security, helping to shield your personal information. With knowledge and preparedness, you can recognize and respond quickly to phishing attempts, safeguarding yourself from malicious cyber activity.
How Phishing Scams Work
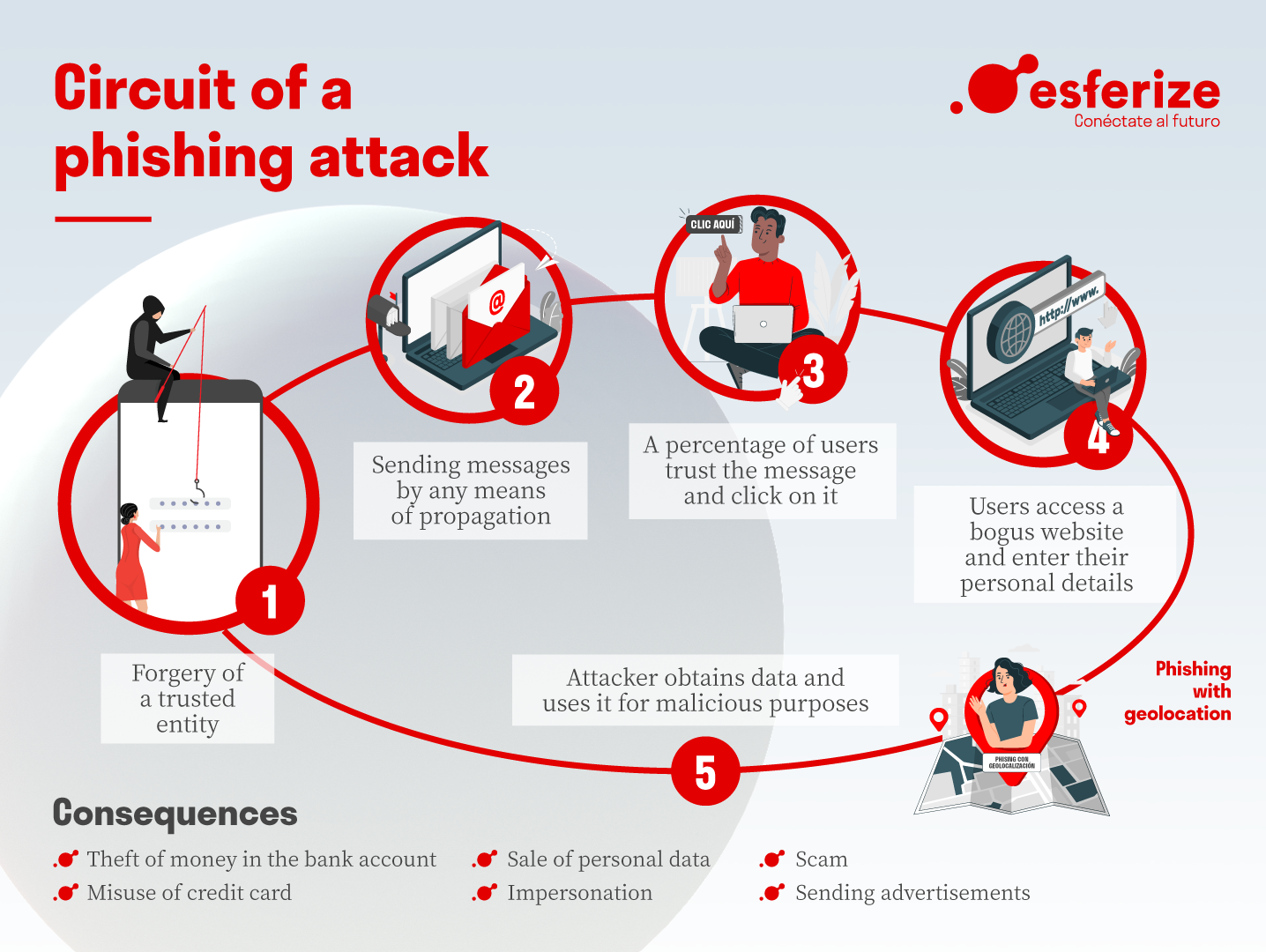
Phishing scams exploit social engineering to trick individuals into revealing personal information like usernames, passwords, and credit card numbers. Scammers impersonate legitimate entities to gain their victims’ trust and achieve their malicious objectives.
The process often starts with deceptive communication, usually through emails or messages that seem to originate from reliable sources such as banks or tech companies. These communications are crafted to create a sense of urgency or fear, prompting recipients to react quickly without scrutiny.
Scammers meticulously replicate brand elements like logos and formatting to lend authenticity to their messages. When victims click on links within these messages, they are directed to fraudulent websites resembling legitimate ones, where they unknowingly enter sensitive information that is harvested by the scammers.
In addition to fake websites, some phishing attempts involve malicious attachments or links that introduce malware on a user’s device. This malware can silently extract data over time or provide unauthorized access to larger networks, resulting in severe data breaches.
Statistics show that 91% of cyber-attacks stem from phishing emails. Therefore, awareness is crucial. Recognizing unsolicited requests for sensitive data and being skeptical of offers that appear too generous or enticing are vital defense tactics.
Understanding the strategies employed in phishing scams empowers users to safeguard their online interactions, ensuring they remain vigilant and protected.
Understanding How Phishing Scams Work
Phishing scams often aim to deceive individuals into divulging sensitive personal information. By learning how these scams operate, you can better protect yourself from potential threats.
The most common tactic involves sending deceptive emails. Scammers masquerade as credible sources such as banks or service providers, crafting emails that prompt recipients to resolve a fabricated issue. These emails typically provide links to fake websites, designed to harvest personal data such as passwords. The emails often include alarming language, warning of account suspension or potential financial loss. Such urgency can cause panic, leading to rushed decisions that compromise your security.
An advanced strategy, known as spear phishing, targets specific individuals. Scammers meticulously research a person’s or an organization’s online activities to craft personalized messages. Tailored to appear credible, these messages can effectively trick individuals, especially those with access to valuable information.
Being aware of how phishing scams work is crucial in safeguarding yourself. By staying informed about these evolving tactics, you can defend against both basic and sophisticated online threats.
Types of Phishing Scams
Understanding how phishing scams work is crucial as they are constantly evolving to outsmart security measures by preying on human weaknesses. Being familiar with the various types can help both individuals and organizations better equip themselves to respond. Let’s explore the most common phishing strategies:
- Email Phishing: This is the most widespread scam consisting of fraudulent emails disguised as credible sources. They urge recipients to click on harmful links, often leading to imitation websites designed to steal login information by inciting urgency or fear of consequence.
- Spear Phishing: Designed to be more specific, this approach targets particular individuals within an organization. Armed with information from research or data breaches, these emails seem legitimate, aiming to infiltrate internal systems.
- Vishing and Smishing: These scams utilize calls and SMS messages to impersonate trusted figures. Vishing often involves someone posing as a banking official seeking personal details, while smishing texts deceive recipients with harmful links or falsified contact information.
- Clone Phishing: This technique replicates genuine emails, altering links or attachments to harmful ones. The resulting familiarity with the email’s appearance makes victims more susceptible to clicking.
- Whaling: A refined form of spear phishing aimed at executives, these attacks present themselves as official business requests to extract sensitive corporate data or initiate unauthorized financial transactions.
By recognizing these scams, individuals can build robust defenses and stay alert to the deceptive tactics employed by scammers. To enhance protection, it is beneficial to turn attention to Phishing Prevention Strategies.
How Phishing Scams Work and Prevention Strategies
Understanding how phishing scams work is crucial for safeguarding against them. By applying strategic prevention techniques, both individuals and organizations can significantly reduce their risk of falling victim to these cunning schemes.
A vital first step is utilizing robust security software. Modern cybersecurity tools can identify and block malicious links and attachments before they reach you. Regular updates ensure your software defends against the latest scams.
In addition, multi-factor authentication (MFA) adds an extra layer of security. By requiring additional verification beyond just passwords, MFA can render stolen credentials useless, providing essential protection for email and sensitive data systems.
Training is equally important. Recognizing phishing techniques enables individuals and staff to spot these scams. Emphasizing signs of urgency or fear in communications can aid in their detection. Simulated phishing exercises enhance awareness and significantly reduce incidents, particularly in organizations that engage in ongoing training.
Creating a clear protocol for reporting phishing attempts encourages prompt action. By fostering a culture where employees report suspicious emails without hesitation, incident response teams can swiftly evaluate and neutralize threats, effectively containing potential breaches.
Integrating these measures ensures comprehensive digital safety by guarding against various phishing tactics. Stay tuned as we explore advanced solutions from AntiPhish.AI in our upcoming section: “Staying Safe with AntiPhish.AI.”
How Phishing Scams Work: Stay Safe with AntiPhish.AI
Phishing scams in today’s digital world are a real threat to our security. Cybercriminals exploit clever tricks to access sensitive data, making it crucial to understand how phishing scams work. Thankfully, AntiPhish.AI provides essential protection, leveraging artificial intelligence to combat phishing attempts effectively.
AntiPhish.AI excels in rapidly scrutinizing emails using AI to identify suspicious elements and alert users to potential threats instantly. By continually adapting to new tactics, it ensures ongoing defense against emerging scams. A seamless Chrome extension enhances this experience, offering smooth browsing and enhanced email security for both personal and professional use without disrupting everyday internet activities.
Users appreciate the extension’s simplicity and reliable warnings, which provide peace of mind. Implementing AntiPhish.AI is a proactive measure that not only explains how phishing scams work but also strengthens your defenses. With technology and awareness, you can stay informed and resilient.
Understanding how phishing scams work is pivotal. The following section will explore strategies for responding effectively to phishing incidents, equipping you to manage any challenges that may arise.
Responding to a Phishing Attempt
Understanding how phishing scams work is essential for protection and swift response if targeted. These scams typically involve emails that trick users into clicking malicious links or sharing personal data, potentially compromising devices and personal information. Acting quickly can mitigate potential harm.
- Disconnect Immediately: If you suspect a breach, disconnect from the network to halt any unauthorized access. Refrain from clicking on unfamiliar links or downloading unknown attachments.
- Update Security Software: Perform a thorough system scan with the latest security software. Phishers often use malware, so timely security updates can detect and eliminate these threats.
- Change Passwords: After any accidental interaction with a suspicious link, update your passwords. Choose strong combinations of letters, numbers, and symbols for enhanced security.
- Notify Authorities: If personal information has been shared, report the incident to relevant authorities like IdentityTheft.gov for tailored recovery steps.
- Monitor Financial Accounts: Regularly review your financial statements for unusual activities. Promptly inform your bank of any discrepancies.
- Report the Scam: Share details of the phishing attempt with your email provider and cybersecurity organizations to aid in preventing future scams.
By staying informed on how phishing scams work and knowing how to respond, you can bolster your defenses and protect against future cyber threats.
Conclusion
Understanding how phishing scams work is crucial in our digital age, where cyber threats are prevalent. This article explored the mechanics of these scams, highlighting how cybercriminals use deceptive emails and fake websites to trick users. We delved into various types of phishing techniques, such as spear phishing and clone phishing, showcasing their differences and specific approaches.
With this knowledge, we discussed effective prevention strategies. These include vigilance towards suspicious emails, verifying the authenticity of information sources, and maintaining strong, unique passwords. Moreover, employing tools like AntiPhish.AI can significantly boost your security by detecting threats at an early stage.
In the unfortunate event that you fall victim to a scam, quick action is vital. Reporting the scam and updating your security settings promptly can minimize further risks and damages.
Apply this knowledge consistently to safeguard your online presence. Regularly educate yourself and others about phishing, remain vigilant, and adopt wise online practices. Remember, your online safety is largely in your hands; stay informed, cautious, and proactive.
By understanding how phishing scams work, you’re not only protecting yourself but also helping to foster a safer digital environment for everyone.
About AntiPhish.AI
AntiPhish.AI is a cutting-edge Chrome extension specifically designed to shield Gmail users from phishing attacks by meticulously analyzing email content, sender information, and embedded links to identify and thwart malicious activity. Offering real-time protection through sophisticated AI-driven algorithms, the platform ensures user-friendly navigation and seamless integration—keeping your sensitive information safe from cybercriminals and identity thieves without requiring technical expertise.
In a digital age rife with cyber threats, AntiPhish.AI stands as an essential tool in preserving the security and integrity of your personal communication, making it a crucial asset for anyone concerned about their online privacy.
Protect your inbox now and experience unparalleled email security with AntiPhish.AI!